Basics of AWS IAM: How to setup a Cloud Trail?

In this blog post, I am going to show you how to create a simple CloudTrail in AWS.
Cloud Trail: Cloud Trail is a service in AWS that logs in the activity of an event in an account. The logging can be done by anyone user/service/role and it generally logs management and data events.
Cloud Trail is activated by default and can store the latest 90 days events. If you want to log the trail in an S3 bucket then we need to create a trail.
Except for global services like STS, IAM and Cloud front the cloud trail is regional.
Now let us see a simple way to create a Cloud Trail.
- Login to you AWS account and search for "Cloud Trail" in the search Tab.
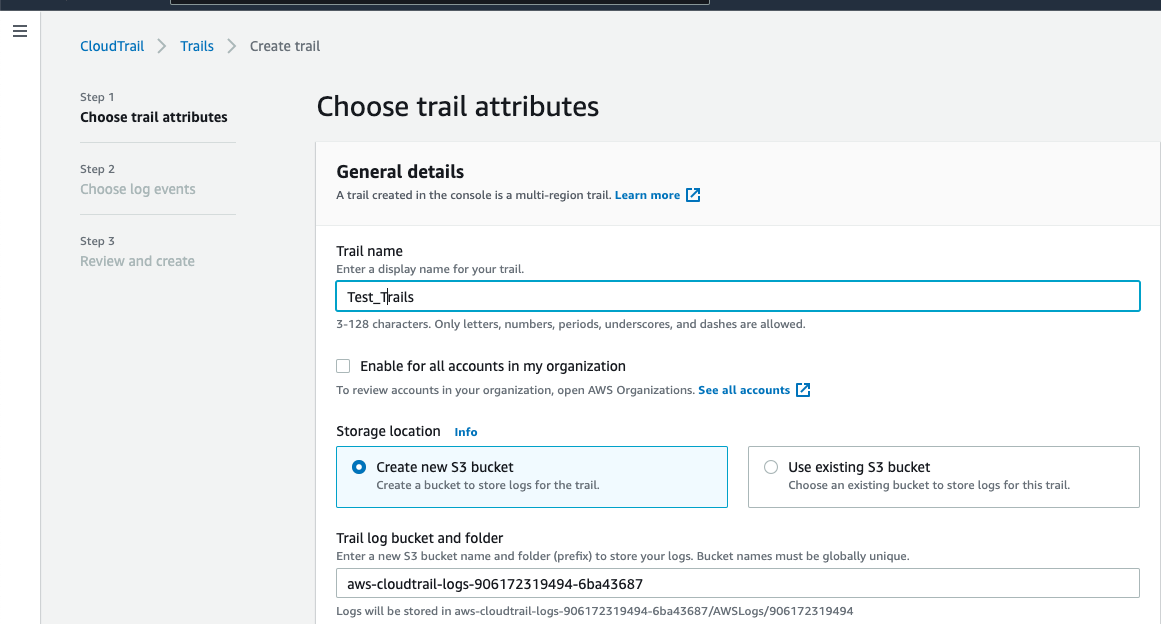
2. Click on the 3 bars at the Top left corner and select trails. Then click on the new trail and enter the name of the trail you wish you give. There is an option to select "Enable for all accounts in my organization" use this if you wish you log the events across your organization in a single place. This can be done only if you create this trail in your management account.
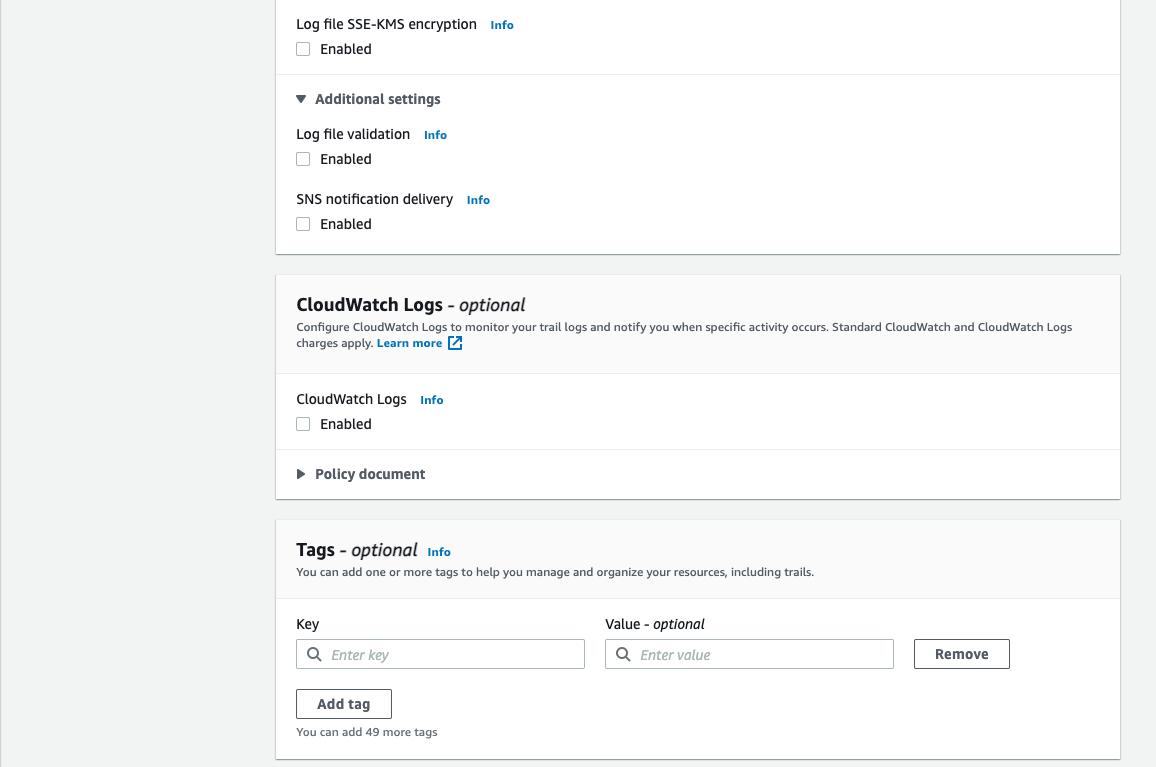
3. I have chosen to untick both the log file SSE KMS Encryption and log file validation. Click Next.
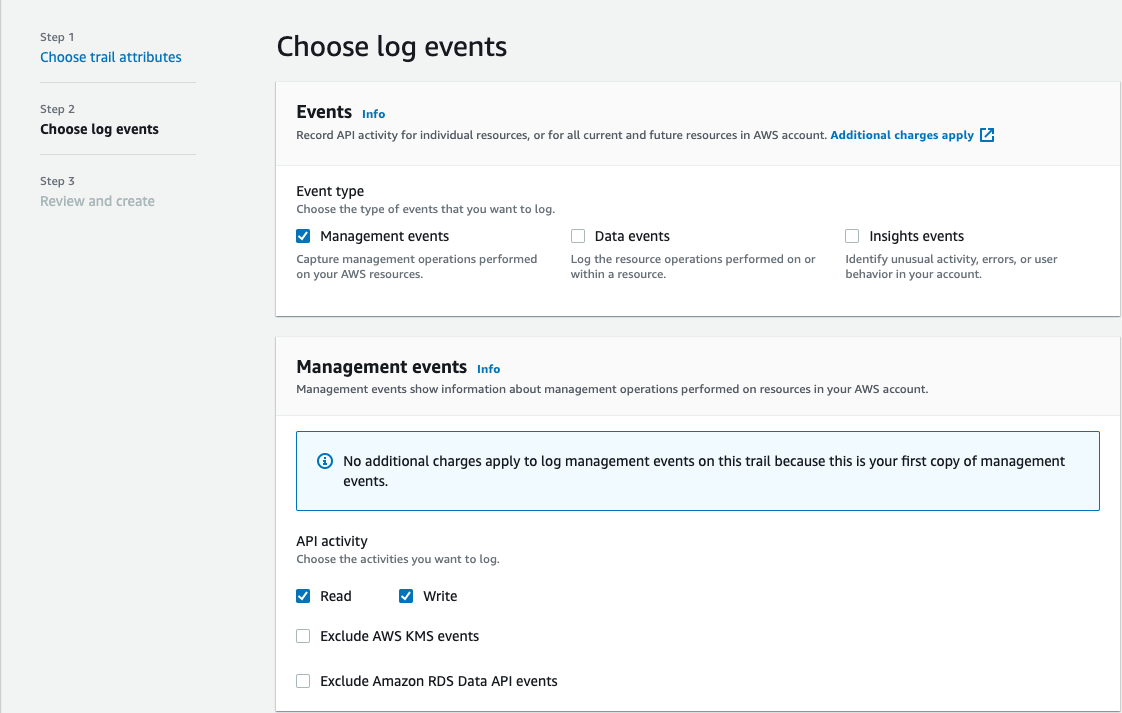
4. I have left everything as default as I only want to log Management events.
5. Verify all the details mentioned in the next step and click create trail.
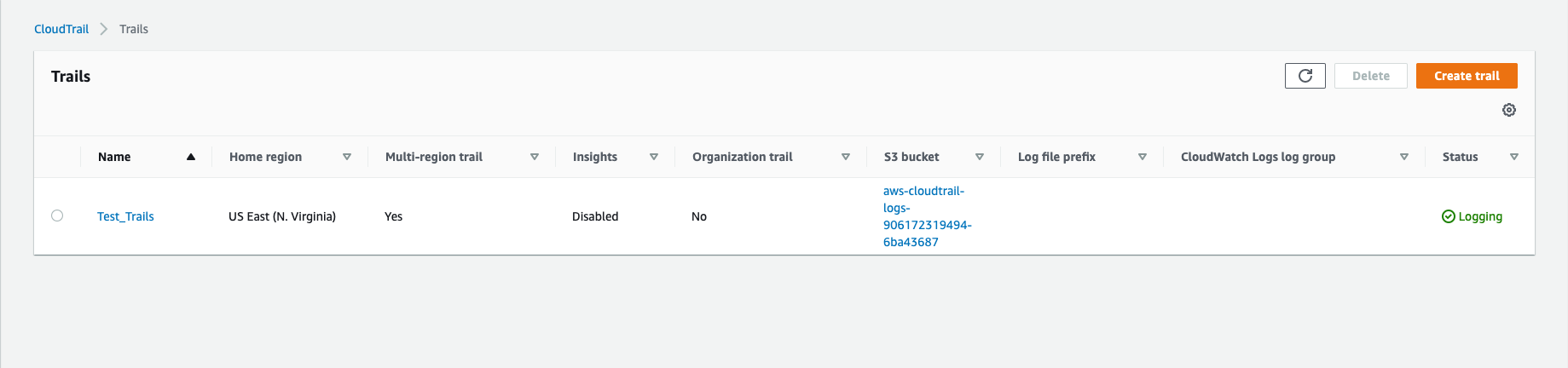
Give a few minutes for the cloud trail to collect logs on the activity done inside the AWS account.
6. Click on the S3 bucket to see the cloud trail logs that are generated in the account.
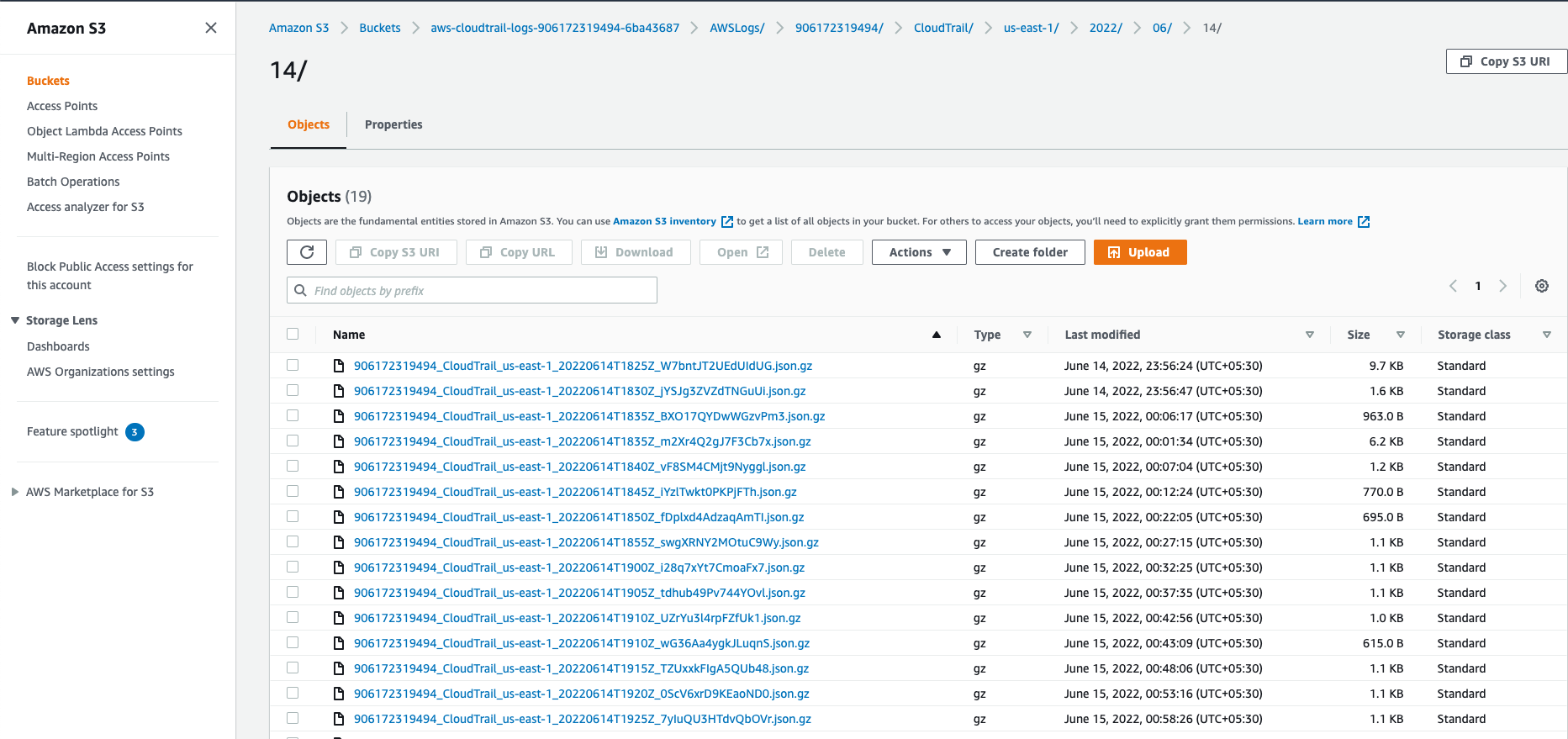
7. Over time logs get created in the S3 bucket and you can see the contents when you open them. Below is an example of the same.
